Configuring AnyConnect WebVPN on Cisco Router |
- Configuring AnyConnect WebVPN on Cisco Router
- Bank customers warned after breach at Epsilon marketing firm
- Rogue Android app sent personal info to legit version's developer, claims AVAST
- UberSocial fixes direct-message privacy bug
- Bank of America to further ramp up security with new CISO
- Comodo compromise expands, hacker talks
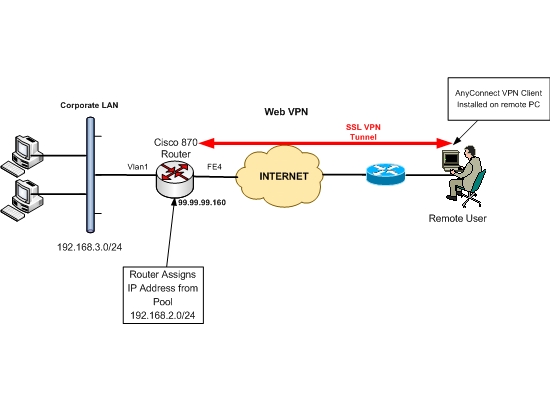
| Configuring AnyConnect WebVPN on Cisco Router Posted: 02 Apr 2011 12:19 PM PDT In this post I will explain how to configure WEB VPN (or sometimes called SSL VPN) using the Anyconnect VPN client on a Cisco 870 router. Web Based VPN has three Remote Access modes: Clientless – You connect to a web page portal from which you can have access to web based applications, File Sharing and Outlook Web Access (OWA) inside the corporate network . Thin client – This mode allows TCP Port- Forwarding on applications, such as Telnet, SSH, SMTP POP3, Remote Desktop Connection (RDP). It uses a Java applet. This mode may be used only on TCP Based Applications. Tunnel Mode or AnyConnect VPN client – almost same as an Easy VPN Client (IPSEC VPN client). In this mode you must have Administrator permissions on your remote access laptop/PC and any IP based Application can be used through this mode. A Java client is downloaded to the user's PC and facilitates the security and encryption from the remote user towards the termination device (router or firewall). Both ASA and Cisco IOS Routers support web vpn technologies. On ASA an extra license is required if you want to have more than two users for your remote access web vpn. Without purchasing any license it provides support for only two users. We will be using the following Network diagram in our example:
Requirements for Anyconnect VPN:
Used in Lab for this tutorial:
Configuration.
!Configure Certificate crypto pki trustpoint local !Generate Certificate and turn on HTTPS Service crypto pki enroll local !Before starting the actual configuration of Web Vpn, first we configure Gateway, on which IP address we shall terminate the Anyconnect VPN, which certificates to use, on which port we shall run the VPN and any redirections necessary ( i.e. if request comes on port 80 port, it will redirect the user to port 443). All these are configured under the webvpn mode. ! enable webvpn gateway configuration mode to configure SSL VPN Gateway. ONLY one Gateway is configured in an SSL VPN Network ! configure hostname for SSL VPN; in our example hostname is home !configure IP address and port on which SSL VPN will connect. !Configure SSL Certificate; in our Example this Certificate is Self-signed !configure Redirect. If somebody connects to TCP port 80 it will be redirected to port 443 ! Enable WebVPN Gateway !turn on AAA and for authentication we use local database !Create Local address pool, from which we'll assign IP addresses to anyconnect clients. !Create loopback interface, if we want to announce this network in any dynamic protocol. !Create access list, which later will be used to control what the webvpn client will be allowed to access. This is not access list for Split Tunneling. Split Tunnel is created in context configuration mode. !After this we need to create a profile context. ! change default Title ! Verify SSL Certificate. ! Change default login message displayed on login page before user login. !Configure policy for this group with name networkstraining !configure banner to be displayed after successful login ! enable tunnel support for the remote user. If the Cisco AnyConnect VPN Client software package fails to install, the remote user can continue to use clientless mode or thin-client mode. ! Below we configure an SSL VPN tunnel access filter which uses the ACL we have created above. Gives us the opportunity to control which type of traffic must allow or block via access list. In our example we created webvpn-acl access list, which permits access from network 192.168.2.0/24 to TCP 3389 ( Remote Desktop Protocol ) of host 192.168.3.100 and all the rest are blocked. filter tunnel webvpn-acl ! Configure IP address pool. When client is connected via anyconnect client an IP will be assigned from this pool. ! Configures the domain for a policy group. ! To install Cisco any connect client on User's PC. When this feature is not turned on, when user is disconnected then Cisco anyconnect client will be automatically uninstalled. svc keep-client-installed !In case of successful authorization it will show us URL below !Configures the tunnel key to be refreshed by initiating a new tunnel connection ! Below is the split tunnel configuration which specifies the destination network to permit access within the tunnel when the user connects via Cisco anyconnect client. If we don't indicate this parameter, then there will be Full Tunnel, meaning that all traffic will pass through the Cisco web VPN Server !Default group !The name of authentication group. We've already created AAA group named webvpn and here this group will be used ! Bind this context to Gateway created above gateway soho After the above we need to install anyconnect client to the flash memory of the router. The version of anyconnect client must support the operating system of the users that will be using the anyconnect service.
After this we check if anyconnect cliet installation was successful in our configuration. ! |
| Bank customers warned after breach at Epsilon marketing firm Posted: 01 Apr 2011 03:57 AM PDT |
| Rogue Android app sent personal info to legit version's developer, claims AVAST Posted: 01 Apr 2011 12:08 AM PDT |
| UberSocial fixes direct-message privacy bug Posted: 31 Mar 2011 10:45 PM PDT |
| Bank of America to further ramp up security with new CISO Posted: 31 Mar 2011 10:00 PM PDT |
| Comodo compromise expands, hacker talks Posted: 01 Apr 2011 08:49 AM PDT |
| You are subscribed to email updates from "Cisco" via Ehsan in Google Reader To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |












0 comments:
Post a Comment